Teachers and Examiners (CBSESkillEduction) collaborated to create the Networking and Internet Class 11 Notes. All the important Information are taken from the NCERT Textbook Web Application (803) class 11.
Networking and Internet Class 11 Notes
Bell proposed the idea of communication through telephone lines in 1876, which led to the creation of the Public Switched Telephone Network (PSTN) in 1877. The US Department of Defense became aware of the necessity of creating a network by joining together geographically dispersed research computers. As a result, the Advanced Research Projects Agency Network (ARPANET) was created in 1969. Digital packet switching was a technology used by ARPANET. Its use was first limited to noncommercial endeavor’s like the military and research. TCP/IP (Transmission Control Protocol/Internet Protocol) was created in 1970 in response to the need for communication among multiple heterogeneous networks. In addition to various smaller networks, NSF created NSFNET, a sizable network, in 1984.
Basic Networking Concepts
A network is any collection of independent computers that communicate with one another over a shared network medium.
Need for Networking
Resource Sharing – Sharing hardware and software resources is made possible by networking computers. Printer, scanner, and memory are three examples…
Communication – Information sharing between network nodes is facilitated by connecting computers through a network. For instance, because the printer is linked to every network node, any of the computer systems can send data to any of the three computer systems or to the printer.
Access to remote databases – A regular individual can easily access any remote database, such as airline bookings, and book tickets.
Requirements of a network
- At least two computers
- Network Interface Cards (NIC) A connection medium, usually a wire or cable, although wireless communication between networked computers and peripherals is also possible.
- Network Operating system soft Novell NetWare, Unix and Linux
Network Terminologies
Nodes (Workstations) – Any network device that can receive and deliver data from one endpoint to another using a connection point is known as node, such as a router, printer, or switch.
Server – The server is a computer that enables the exchange of data, software, and hardware resources through a network. There are two types of Server –
Dedicated Server – These are generally used on big network installations where one computer is reserved for the dedicated task.
Non – dedicated Server – A workstation can function as both a client and a server in small networks.
Network Interface Unit – Each workstation and the server have a network interface unit attached to them, which aids in establishing connection between the server and workstations.
Switching Techniques
In order to efficiently send data across the network, switching mechanisms are used. Circuit switching and packet switching are the two switching methods now used to enable communication between two computers on a network.
Circuit switching – Circuit switching is a style of network design in which a physical path is acquired and allocated for the duration of a dedicated connection between two endpoints in the network. Circuit switching is used in standard voice phone service. The duration of a call is when this reserved circuit is utilised.
Packet switching – Small data packets are sent between different networks using packet switching. These data “packets” or “chunks” enable quicker, more effective data transport. When a user transfers a file over a network, it frequently travels in smaller data packets rather than all at once.
Data communication terminologies
Channel – The medium over which a message is transmitted from one location to another is known as a communication channel. It is a channel that allows data to be transmitted between distant devices, to put it simply. The complete physical medium, such as a phone line, optical fibre, coaxial cable, or twisted pair wire, may be referred to as a communication channel.
Bandwidth – The most data that can be sent through an internet connection in a specific amount of time is known as Bandwidth. It is actually the amount of data that can be delivered across a connection in a given amount of time, measured in megabits per second (Mbps). Modal.
The data transfer rate – The speed at which a device or network component can send and receive data is referred to as a data transfer rate (DTR).
Network Types
On the basis of geographical span, the network can be broadly categorized as PAN, LAN, MAN, and WAN.
Personal Area Network – A personal area network (PAN) is a type of computer network designed to connect computers and other devices that are near to a single user. Personal computers, printers, fax machines, telephones, PDAs, scanners are the example of Personal Area Network.
Local Area Network – When a network is established within a restricted geographic area, it is referred to as a local network. Private networks with a radius of up to 1 km. They are typically established on a campus or in a building. LANs function at speeds between 10 Mbps and 1 Gbps.
Metropolitan Area Network – A single organisation, a large group of people, or many different people or organisations may own a metropolitan area network (MAN). These networks, which have a radius of up to 50 km, are used to create connections within cities.
Wide Area Network – The WAN (wide area network) covers roughly 1000 km. They are useful for linking isolated places and for long-distance communication. They create connections inside a nation or continent.
Networking Concepts – II
A transmission medium is a channel of transmission used to send signals carrying data from one node to another. The data is converted into an appropriate form for transmission on the medium via a signal.
Guided Medium – Physical conductors like twisted pairs, coaxial cable, and fibre optics are referred to by this phrase. The signal travels as voltage and current in coaxial and twisted pair cable but as light in optical fibre.
Unguided Medium – Electrons are used by the unguided medium instead of a physical conductor. Microwave, radio waves, and infrared are a few examples of unguided media.
Network Topologies
Network topology refers to a network’s configuration of notes. Broadly speaking, there are two different topologies: broadcast and point-to-point.
Broadcast Topology – Broadcasting information typically refers to sending it to numerous receivers. In the same way that a radio station sends a signal to its many listeners, a TV provider broadcasts a signal to digital TV customers.
Point – to – point Topology – The simplest topology is point to point, which uses a shared link to directly connect two nodes. Transmission between such two nodes is limited to using the total available bandwidth of the common link.
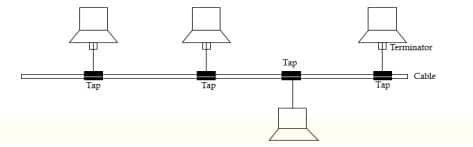
Bus Topology
Bus topology, often called line topology, is a type of network topology in which each device is connected to the network by a single coaxial or RJ-45 network wire.
Ring Topology
In a ring topology, every device is connected via a wire that forms a ring. The intended recipient of the message is reached by way of a one-way transmission of the intended message. Device addition and deletion, as well as fault isolation and detection, are simple processes.

Star Topology
All of the devices in a star topology are linked to a central controller called a hub since communication between any two devices occurs through the hub. Installation and configuration of the Star network are simple. Furthermore, fault isolation and detection are simple.

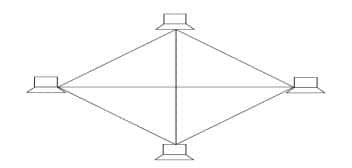
Mesh Topology
Every node in the network is connected to every other node thanks to mesh topology. The topology offers secure data transport without any triffic issues because to dedicated point-to-point connections between every feasible pair of nodes.
Tree Topology
A hybrid topology that combines bus and star topologies is called tree topology.
In a bus topology, backbone cable functions as the tree’s stem, while star networks (and even individual nodes) are connected to the primary tree by star cables.

Network Devices
Creation of a network requires various network devices, each of which plays a specific role in the network.
Repeater – A signal may weaken and degrade with increased distance. In order for the input signal to return to its original form and cover a greater distance, a repeater is required.
Hub – A hub is a computer device’s connection point where data from various ways converge before being delivered in various directions to the appropriate devices. By stopping specific data packets from travelling to a destination, a hub can also function as a switch.
Bridge – A bridge is a multiport network interface used to connect two or more LANs, sometimes at differing speeds. Therefore, a bridge can be used to combine smaller LANs to create a larger LAN.
Switch – Switches are used to connect individual nodes in the network with one another, as opposed to bridges, which join two or more LAN segments. Each node in the network is linked to a different switch port.
Router – Switches are used to connect individual nodes in the network with one another, as opposed to bridges, which join two or more LAN segments. Each node in the network is linked to a different switch port.
Gateway – A gateway enables communication across networks based on various protocol systems. Data from one network that uses one protocol is translated to the outgoing network’s protocol before being forwarded. As a result, a gateway can be compared to a router that has software for protocol conversion.
RJ-45 – RJ-45, the abbreviation for Registered Jack, is used to link computers on LANs, particularly Ethernet LANs. RJ connectors resemble RJ equipment in appearance, however they are a little wider.
Wi-Fi Card – Wi-Fi cards are small and portable cards that allow your desktop or laptop computer to connect to the internet through a wireless network.
Network Protocols
Transmission Control Protocol (TCP) – For communication via a network, TCP is a well-known communication protocol. Any communication is split up into a number of packets that are transferred from the source to the destination, where they are reassembled.
Internet Protocol (IP) – The process or technique used to transmit data from one computer to another via the internet is known as Internet Protocol (IP). Every computer on the internet, referred to as a host, has at least one IP address that distinguishes it from every other computer there.
Point-to-Point Protocol – One computer system is connected to another using the TCP/IP protocol known as Point-to-Point Protocol (PPP). PPP is a protocol that computers use to communicate across landlines and the Internet. When two systems are physically linked by a phone line, a PPP connection is created.
HyperText Transfer Protocol (HTTP) – Resources are transferred across the internet between client devices and servers via the HTTP protocol. Client devices ask servers for the resources required to load a web page; the servers respond by sending the client devices the requested resources.
File Transfer Protocol (FTP) – The file transfer protocol is a method for downloading, uploading, and moving files between computer systems and across the internet. File transfers between computers or via the cloud are made possible through FTP.
Simple mail transport Protocol (SMTP) – Outgoing email can be sent and distributed via SMTP. The SMTP protocol is dependable and simple to set up. Either messages reach their intended destination or an error message notifying them of the situation.
Post office Protocol (POP) – Incoming emails can be received via POP3. A popular way of getting email that receives and retains email for a person until they pick it up is known as Post Office Protocol 3 (POP3).
Telnet – The primary internet protocol for connecting to distant machines is telnet. It enables TCP/IP network connections to remote computers.
Internet Relay Chat (IRC) – IRC protocol is used for chatting. The message is passed between clients via the IRC server.
Voice over Internet Protocol (VoIP) – Instead of using a public switched telephone network, it makes it possible to transport voice over a packet switched network. Phone calls can be made utilizing a regular internet connection by using VOIP software. Today, there are three major types of VoIP service that are frequently used – ATA, IP phones, Computer-to-computer.
Web Architecture
Before a website is designed, developed, and launched, its technical, functional, and aesthetic components are planned and designed as part of its website architecture. It is a tool that website designers and developers use to create websites.
Types of web architectures
Client-server model
Clients and servers made up the first two tiers of the web’s architecture. The functions and services that the system was designed to provide were shared by clients and servers. For instance, the client might ask the server for a service, and the server would then respond by offering the requested service.
Three-tier model
Three-tier architectures have an application logic that handles data processing and permits some interaction between the client and the server. For instance, a database server is just used for data storage, whereas an application server can process data. This allows for the dynamic loading and saving of content. The client’s behavior is frequently dictated by the scripting language JavaScript.
Service-oriented architectures (SOA)
The web is being utilized to connect internationally dispersed IT structures. The client-server model is much simpler than the complexity of modern IT and online applications. Business processes can be automated using SOAs by the systems involved talking with one another, sometimes without human intervention, and carrying out specific duties. Online marketplaces, e-commerce, e-learning, online banking, and business intelligence applications are a few examples.
MAC Address
Each device on a network has a unique identity known as a Media Access Control address (MAC address). It is primarily assigned by the manufacturer. They are frequently located on the network interface controller (NIC) card of a device.
IP Address
Every computer in a network has an additional distinctive identification code called an IP Address. The four bytes (or 32 bits) that make up an IP address can range in value from 0 to 255. A typical IP address appears as follows:
59.177.134.72
Domain Name
Consequently, we may use a computer’s IP address whenever we need to speak with it online. However, it is virtually difficult for anyone to keep track of all the computers’ IP addresses with whom they might need to interact. As a result, a system that gives names to some computers (web servers) and keeps a database of these names and associated IP addresses has been created.
Generic Domain Names:
·com – commercial business
·edu – Educational institutions
·gov – Government agencies
·mil – Military
·net – Network organizations
·org – Organizations (nonprofit)
Country Specific Domain Names:
.in – India
·au – Australia
·ca – Canada
.ch – China
.nz – New Zealand
.pk – Pakistan
.jp – Japan
.us – United States of America
Domain Name Resolution
The process of translating domain names into IP addresses is known as domain resolution. The DNS server is responsible for domain name resolution. Domain resolution is also referred to as domain pointing, server configuration, reverse IP registration, and other similar terms.
Network Threats and Security Measures
Malwares
Malicious software (programmes) that are intended to harm the system or to gain unauthorised access to it, interfere with regular system performance, or prevent authorised users from using computing resources are referred to as malware. Malware includes viruses, worms, and Trojan horses.
Virus – A virus is a piece of software code that can damage your computer by corrupting or overwriting system data. A computer virus behaves similarly to viruses that impact human bodies by replicating and harming cells.
Worm – A worm is frequently acquired via a network, and it floods the hard disc by automatically producing several copies of itself there. It causes network congestion when a worm is received as an email attachment and automatically forwarded to the recipients.
Trojan Horse – A Trojan Horse is a piece of code that makes the system seem desirable and useful but actually does the opposite. A Trojan horse can integrate with a reliable programme. For instance, it might be included with any game that you download from the Internet.
Eavesdropping – The act of secretly or covertly listening to another person’s private discussion or communications without that person’s agreement is known as eavesdropping. Telephone lines, cell phone networks, email, and instant messaging are all used for eavesdropping.
Denial of Service – A denial-of-service attack (DoS attack) is a cyber-attack in which the machine or network resource becomes unavailable to its users by temporarily or indefinitely
disrupting services.
Phishing – The practice of stealing a user’s personal information through fraudulent mail is known as phishing. These emails either include embedded forms that request personal information from you or include links to web pages that might ask you for it. There may be attempts to steal passwords, bank account numbers, debit/credit card numbers, and other sensitive information.
Cyber Crime
Cybercrimes are the crimes related to the misuse of computers or the Internet such as theft, fraud, and forgery. Some of these crimes are mentioned below
- Sending spam mails to uninterested recipients.
- Hacking someone’s account or system.
- Stealing someone’s personal information through phishing
- Hosting a site carrying lots of malwares or being a source for spreading them.
- Harassing someone through mails, messages or social networking.
- Posting offensive content on any site or sending it to anyone.
- Defaming someone using the Internet.
- Forging someone’s digital signatures
- Indulging in fraudulent financial transaction
- Providing misleading information to clients/ general public through use of Internet resources
- Intellectual Property theft
- Illegal downloads, plagiarism
Network Security Tools and Services
Firewalls – An enterprise, home, or individual’s internal network is protected by a firewall from malicious traffic coming from other networks.
Antivirus – Antivirus software works to safeguard your computer from harmful and potentially undesirable programmes. It is in charge of looking for and deleting these malicious programmes in order to keep the system safe.
Password managers – A password manager is a piece of software that aids in organising and storing passwords.
Protective Measures while accessing Internet
- Never click on a suspicious link specified on a web page or send through a mail for which you are not sure about its authenticity.
- Make sure that passwords are strong and are changed frequently.
- Never disclose personal information such as date of birth, home address, personal phone number, account details, passwords, credit and debit card details, work history details.
- Report phishing issues to the concerned authorities or at cybercrime.gov.in. In case of unsolicited mails, mark them as spam mails.
- Secure HyperText Transfer Protocol (HTTPs) is a secure version used for communication between client and host on the Internet.
- Ensure that the web browser being used for accessing the web is updated and is secure.
- Beware before spreading any kind of a rumor as it may be treated as a cybercrime.
- If someone is harassing or threatening you, take a snapshot of it as a proof, and block the person. Also, report the incident to the site administrator
- Use updated antivirus and firewall, secure browsing, and password management techniques.
Cyber Law
Cyber laws are the laws for systematic use of e-resources, for example, e-business, and serve as a measure against illegal cyber-crime.
Cyber offenses under IT Act
- Tampering with computer source documents – Section 65
- Hacking -Section 66
- Publishing of information which is obscene in electronic form -Section 67
Intellectual property rights (IPR) Issues
Intellectual property rights are the rights given to an individual over the invention of their own.
Patent – An invention is a product or a technique that, in general, offers a new way of doing something or presents a new technical solution to a problem. A patent is an exclusive right awarded for an invention. Technical details concerning the innovation must be made public in a patent application in order to obtain one.
Trademark – A trademark is characterized as a name, a different sign, or a tool used to distinguish a good or a service. A particular person or business produces or offers the goods or service.
Copyright – A written document is referred to as having copyright. The violation of copyrights may result in legal action. The following type of work is eligible for copyright protection. written works any accompanying words for musical works.
Employability Skills Class 11 Notes
- Unit 1 : Communication Skills – III
- Unit 2 : Self-Management Skills – III
- Unit 3 : Information and Communication Technology Skills – III
- Unit 4 : Entrepreneurial Skills – III
- Unit 5 : Green Skills – III
Employability Skills Class 11 MCQ
- Unit 1 : Communication Skills – III
- Unit 2 : Self-Management Skills – III
- Unit 3 : Information and Communication Technology Skills – III
- Unit 4 : Entrepreneurial Skills – III
- Unit 5 : Green Skills – III
Employability Skills Class 11 Questions and Answers
- Unit 1 : Communication Skills – III
- Unit 2 : Self-Management Skills – III
- Unit 3 : Information and Communication Technology Skills – III
- Unit 4 : Entrepreneurial Skills – III
- Unit 5 : Green Skills – III
Web Application Class 11 Notes
- Networking and Internet Class 11 Notes
- Website Development using HTML and CSS Class 11 Notes
- Multimedia Class 11 Notes
- JavaScript Class 11 Notes
Web Application Class 11 MCQ
- Network and Internet Class 11 MCQ
- Web Designing with HTML and CSS MCQ Questions
- GIMP Class 11 MCQ Questions
- JavaScript Class 11 MCQ