The Cyber Law Class 11 Exercise Solutions are designed to help HSC students understand textbook questions and answers related to cyber laws in a simple and structured manner. These solutions are prepared strictly according to the Maharashtra State Board (HSC) Information Technology syllabus and follow the latest exam pattern.
Cyber Law Class 11 Exercise Solutions
Q 1. Complete the following web.
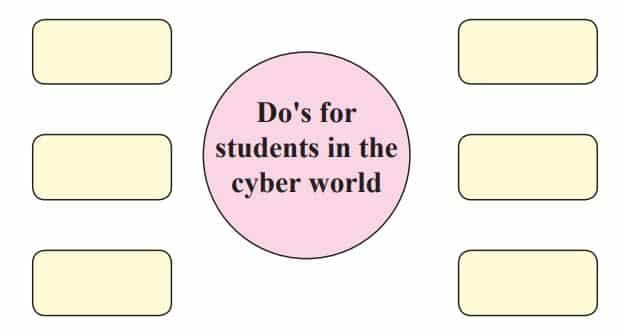
Answer:
- Use strong and unique passwords
- Log out from shared devices after use
- Report suspicious messages or emails
- Keep personal information private
- Update software and antivirus regularly
- Be respectful and kind online
Q 2. Complete the following chart.
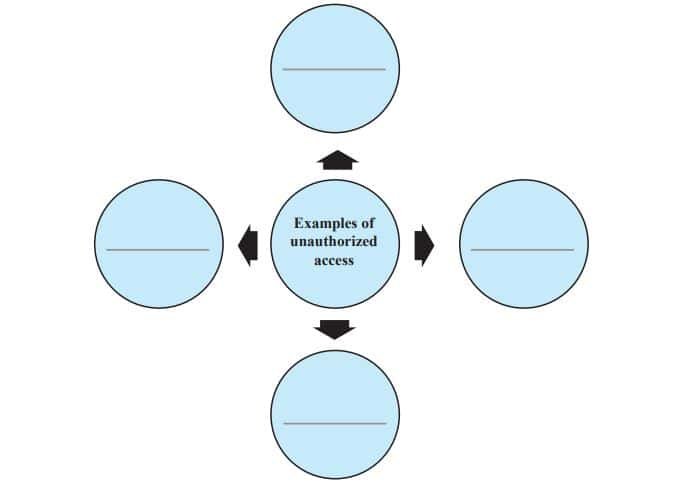
Answer:
- Hacking into someone’s account
- Using another person’s password without permission
- Accessing confidential files without authorization
- Installing spyware or keyloggers secretly
Q3. Fill following boxes with appropriate cyber crime name
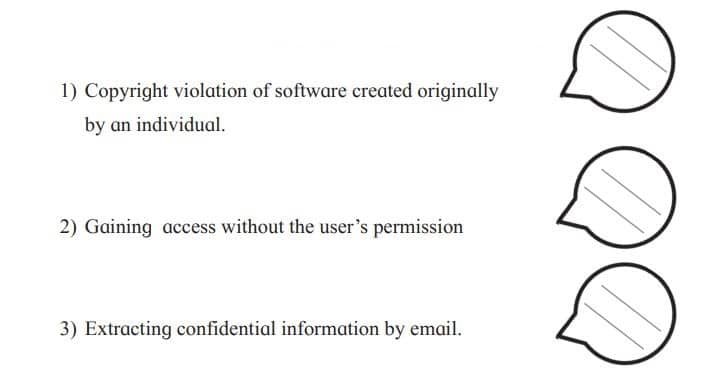
Answer:
| Copyright violation of software created originally by an individual | Software Piracy |
| Gaining access without the user’s permission | Hacking |
| Extracting confidential information by email | Phishing |
Q 4. Read the following and answer the question.
Rahul lost his pen drive in his college computer lab. His classmate Madhav finds it .He carries it home to return it to him the next day. When Madhav opens it he finds his favourite game. He thinks of making a duplicate copy of the game software.
I) Does Madhav think ethically ?
II) What do you think should Madhav do ?
III) If he makes a duplicate copy then which cyber crime will he commit ?
Answer:
I) Does Madhav think ethically ?
Answer: No, Madhav does not think ethically.
II) What do you think should Madhav do ?
Answer: Madhav should return the pen drive to Rahul without opening or copying anything.
III) If he makes a duplicate copy then which cyber crime will he commit ?
Answer: He will commit Software Piracy.
Q 5. Answer in brief
1) What care should be taken by the user while doing online activities ?
Answer: The user should be take care while doing online activities-
- Follow copyright rules when downloading.
- Report online bullying quickly.
- Use strong, unique passwords and change them often.
- Download software only from trusted sources.
- Sign in only on sites with https://.
2) Define the terms (1) Ethics (2) Moral
Answer:
- Ethics: Ethics, also called moral philosophy, is the discipline concerned with what is morally good and bad, right or wrong.
- Morals: The standards of behaviour; principles of right and wrong behaviour. Thus morals are dictated by society, culture or religion, while ethics are chosen by the person himself, which governs his life. This chapter introduces the dos and don’ts of the cyber world.
3) Explain three examples related to unauthorized access?
Answer: The three examples of unauthorized access are-
- Hacking into someone’s email account without permission.
- Using another person’s password to log into their social media.
- Accessing confidential files on a computer system without authorization.
4) Explain software piracy and Hacking
Answer: Software piracy is nothing but copyright violation of software created originally by an individual or an institution. Example: When you download a copy of licensed software. Hacking refers to unauthorised intrusion into a computer or a network.
Q.6. State true or false
1) Firewall is used to encrypt transmission of data.
Answer: False
2) The standards of behaviour; principle of right or wrong is referred as moral.
Answer: True
3) Hacking bank account related information is an example of software piracy.
Answer: False
4) Phishing is representing some one else’s work as own without permission.
Answer: False
Q.7 Match the following.
| A | B |
|---|---|
| (1) Copying a game file | (a) Firewall |
| (2) Law related to internet | (b) Cyber threat |
| (3) Network security | (c) Software piracy |
| (4) System crashes suddenly | (d) Cyber Law |
Answer:
| A | B |
|---|---|
| (1) Copying a game file | (c) Software piracy |
| (2) Law related to internet | (d) Cyber Law |
| (3) Network security | (a) Firewall |
| (4) System crashes suddenly | (b) Cyber threat |
Q 8. Observe the following picture and give your opinion about it by responding to the following questions.

1) Is ‘B’s response correct or not ?
Answer: No, B’s response is not correct.
2) What will be the consequences of ‘B’s reply ?
Answer: The stranger may Steal money or misuse identity
3) Which type of cyber crime does the picture depict ?
Answer: Phishing or OTP Fraud
Disclaimer: We have provide you with the accurate handout of “Cyber Law Class 11 Exercise Solutions“. If you feel that there is any error or mistake, please contact me at anuraganand2017@gmail.com. The above study material present on our websites is for education purpose, not our copyrights.
All the above content and Screenshot are taken from Information Technology Class 11 Textbook and MSBSHSE (HSC) Support Material which is present in MSBSHSE (HSC) website, This Textbook and Support Material are legally copyright by Maharashtra State Bureau of Textbook Production and Curriculum Research, Pune. We are only providing a medium and helping the students to improve the performances in the examination.
Images and content shown above are the property of individual organisations and are used here for reference purposes only. To make it easy to understand, some of the content and images are generated by AI and cross-checked by the teachers. For more information, refer to the official website.
